Pentesting Android Apps-Part 2 -Static Analysis
In this post I am going to detail how to perform static analysion Android apps recieved by developer.
For my example ,I am going to work with a sample apk named Diva
Open the file with Android Studio
First thing to start when analyzing an Android app is to see the AndroidManifest.xml file
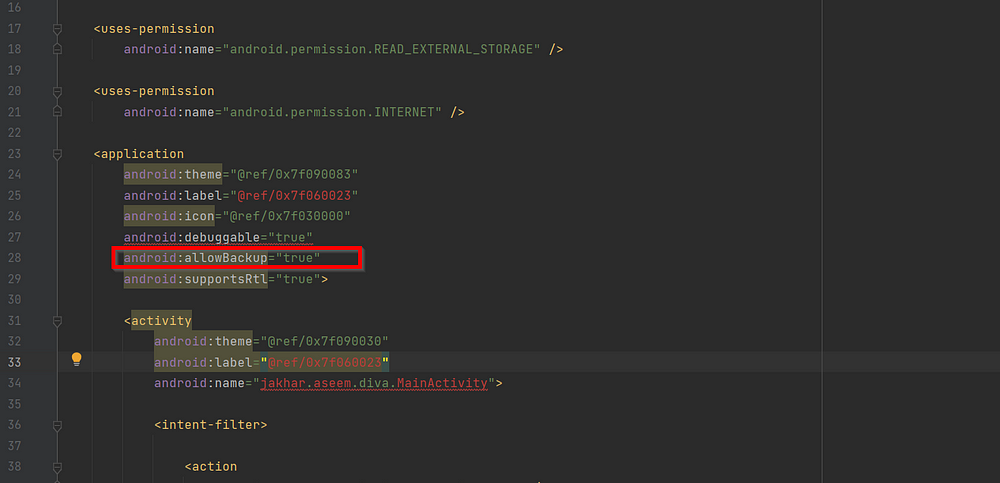
1)Look for allowBackup attribute :
This attribute if set to true can allow backup of your app and then attackers can get private data
Remediation : allowBackup attribute should be set to False
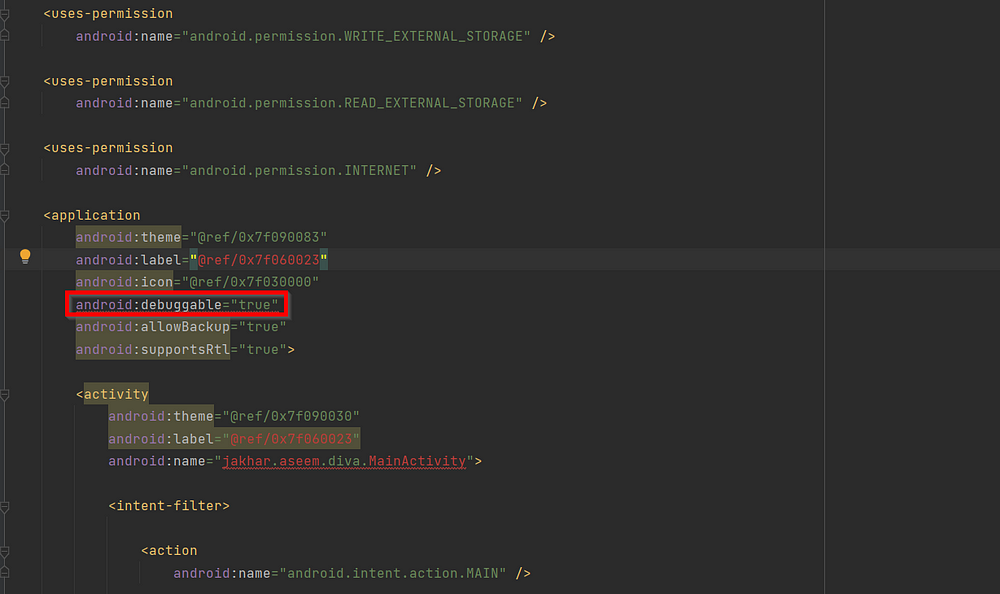
2) Look for debuggable attribute
This attribute determines whether the app is allowed to be debugged.
Remediation : debuggable attribute should be set to False
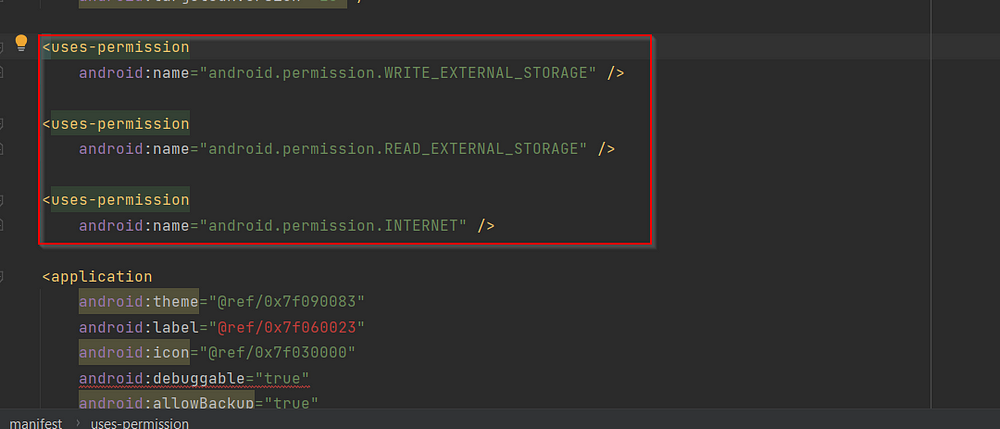
3) Check for insecure permissions
Go through the permissions with the developer to identify the purpose of every permission set and remove unnecessary permissions.
Remediation:Remove any unwanted permissions
Next we will perform reverse engineer the apk file to see the code
Two tools wouldd be required for that :
Dex2jar
Use the command:
d2j-dex2jar.bat “path to apk file”

You get a jar file as output
Now open jd-gui

Open the jar file with jd-gui to see all the classes

Now you can analyze code to find if there are any unwanted data that can be leveraged by attackers.